Published on
The OWASP Top 10 is a valuable resource for the AppSec community, as it outlines the most prevalent vulnerabilities that developers must be aware of.
In this article, we will focus on Cryptographic Failures and advise how to prevent them in your code. We also recommend The Diligent Developer Chronicles as a helpful training resource for your development team.
Read More About OWASP Top 10: OWASP Top 10 Broken Access Control Explained
What are Cryptographic Failures?
OWASP Top 10 Cryptographic Failures are security vulnerabilities that can occur when cryptographic algorithms, protocols, or implementations are incorrectly used. This can expose sensitive data to attackers, such as passwords, credit card numbers, and personal identification numbers.
There are many different ways that cryptographic failures can occur. Some of the most common include:
- Not Using Encryption - Sensitive data should always be encrypted when transmitted over the network or stored on a server.
- Insecure Cryptographic Functions - Cryptographic functions can be implemented insecurely, leading to vulnerabilities.
- Improper Key Management - Cryptographic keys are critical to the security of any system, so it's important to manage them properly.
Read More: OWASP: A02:2021 – Cryptographic Failures
Real-Life Example of a Cryptographic Failure: Exactis LLC.
Exactis is a marketing and data aggregation firm that collects and sells data on millions of people. In 2017, Exactis accidentally exposed a database containing 340 million individual records, including millions of US citizens' names, phone numbers, emails, and other sensitive data.
In the aftermath of the Exactis cryptographic failure, Exactis took steps to improve its data security. The company encrypted databases, secured servers, and implemented new security policies. Exactis also offered free credit monitoring to the people whose data was exposed.
Read the SecurityWeek Article: Massive Breach at Data Broker Exactis Exposes Millions of Americans
How Can You Protect Against Cryptographic Failures
Cryptographic Failures allow attackers to access sensitive data that should be secure. Many things can be done to protect against cryptographic failures, but the key is to use strong cryptographic algorithms and protocols.
Here are some ways you can prevent Cryptographic Failures within your application:
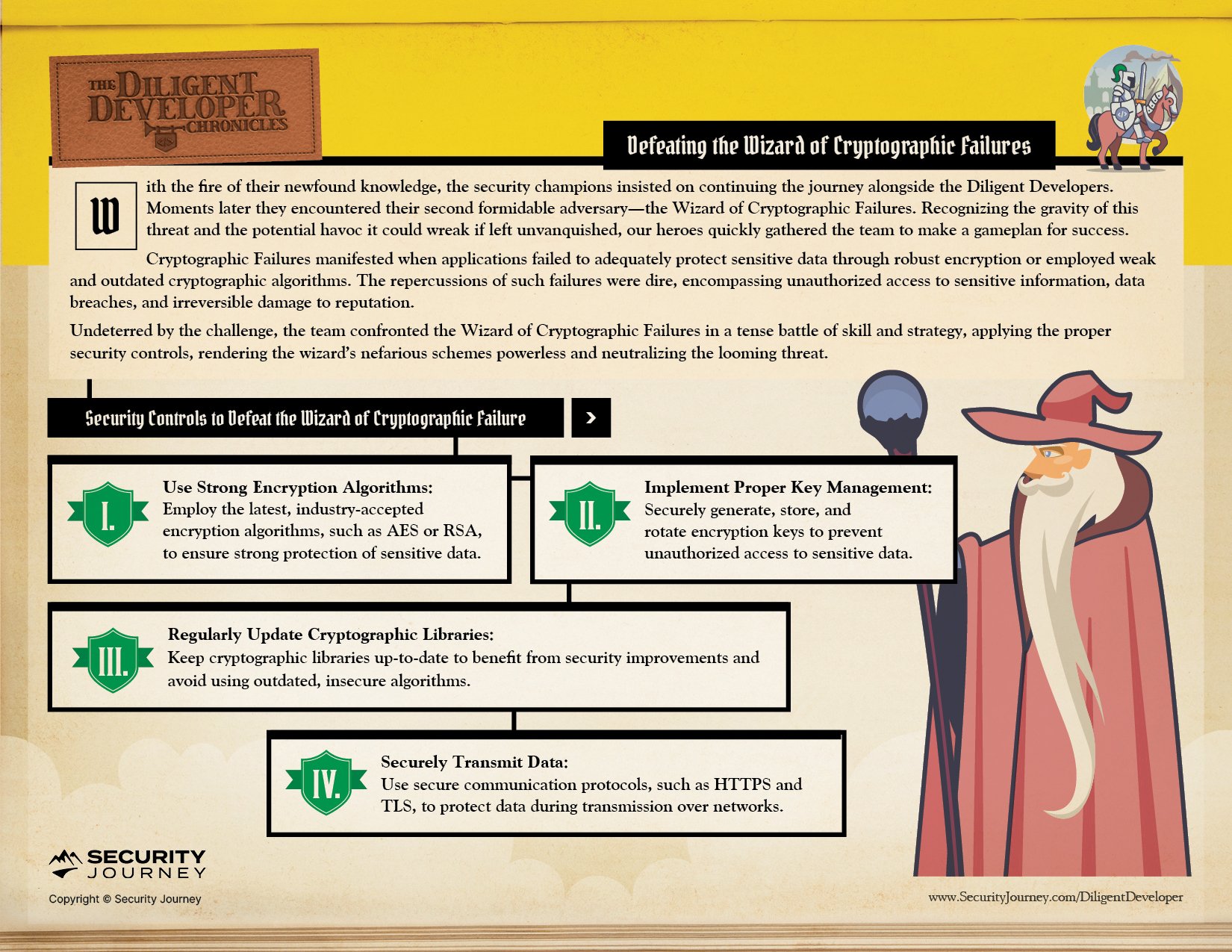
Strong Encryption Algorithms - embracing the latest and industry-accepted standards like AES or RSA to ensure robust protection for sensitive data against malicious actors.
Regularly Update Cryptographic Libraries - This practice enables you to benefit from the latest security enhancements and avoid the usage of outdated and insecure algorithms.
Proper Key Management Procedures - Secure generation, storage, and rotation of encryption keys are paramount in preventing unauthorized access to sensitive data.
Secure Communication Protocols Such as HTTPS And TLS - to safeguard data during transmission across networks.
Bring The Diligent Developers to Your Organization
Our AppSec experts at Security Journey recommend that developers don’t just take annual training on the most current OWASP Top 10 to be aware of prominent vulnerabilities and code risks but to have continuous training and conversations about code security in your organization.
But why not have fun in the process?
Security Journey developed The Diligent Developer Security Awareness & Education Program as a fun way to not only enhance security awareness, but to build skills across your development team to empower them to think securely. This could be added to National Cybersecurity Awareness Month initiatives for the entire development team or be used to grow a security champions program.
In Chapter Two, The Diligent Developers take on The Wizard of Cryptographic Failures:
As The Diligent Developers continue on their journey, stay tuned to see what OWASP Top 10 Challenge they take on next.
Visit our webpage to learn more about accessing program materials and a program guide to train your organization on OWASP Top 10 vulnerabilities effectively.