Published on
The OWASP Top 10 is an essential resource for the AppSec community, highlighting the most common vulnerabilities developers should know. However, even though some vulnerabilities consistently appear on the top 10 list, it can be challenging to become proficient in preventing them.
In this article, we will concentrate on Security Misconfiguration, provide recommendations on how to avoid it in your code, and break down how The Diligent Developer Chronicles is a great training tool for your development team.
Read More About OWASP Top 10: OWASP Top 10 Insecure Design Explained
What is Security Misconfiguration?
Security misconfigurations can occur when security options are not defined to maximize security or when services are deployed with insecure default settings. Security misconfigurations are often overlooked but can be a significant security risk. Attackers can exploit them to gain unauthorized access to systems, data, or applications.
Here are some examples of security misconfigurations:
- Using Default Passwords or Configurations - Using these default settings can make it easy for attackers to gain access to the system.
- Enabling Unnecessary Features - Enabling these unnecessary features can increase the system's attack surface and make it more vulnerable to attack.
- Not Patching Software - Not patching software can leave the system vulnerable to attack.
- Storing Sensitive Data in Clear Text - Storing sensitive data in clear text makes it easy for attackers to access and steal the data.
Read More: OWASP: A05:2021 – Security Misconfiguration
Real-Life Example of Security Misconfiguration: NASA/Jira Exploit
In 2018, NASA was the victim of a security misconfiguration attack that exposed sensitive data to unauthorized users. The attack resulted from an authorization misconfiguration in project management tool, Atlassian JIRA, which allowed attackers to access sensitive information about NASA's projects and personnel.
NASA has since taken steps to mitigate the risk of future attacks, including implementing stricter security policies and procedures and regularly scanning its systems for vulnerabilities.
Read More on ZDNet: NASA Internal App Leaked Employee Emails, Project Names
How Can You Protect Against Security Misconfiguration?
The key to protecting against security misconfiguration is having a strong security culture and implementing strict security policies and procedures.
Here are some ways you can prevent Security Misconfiguration within your code:
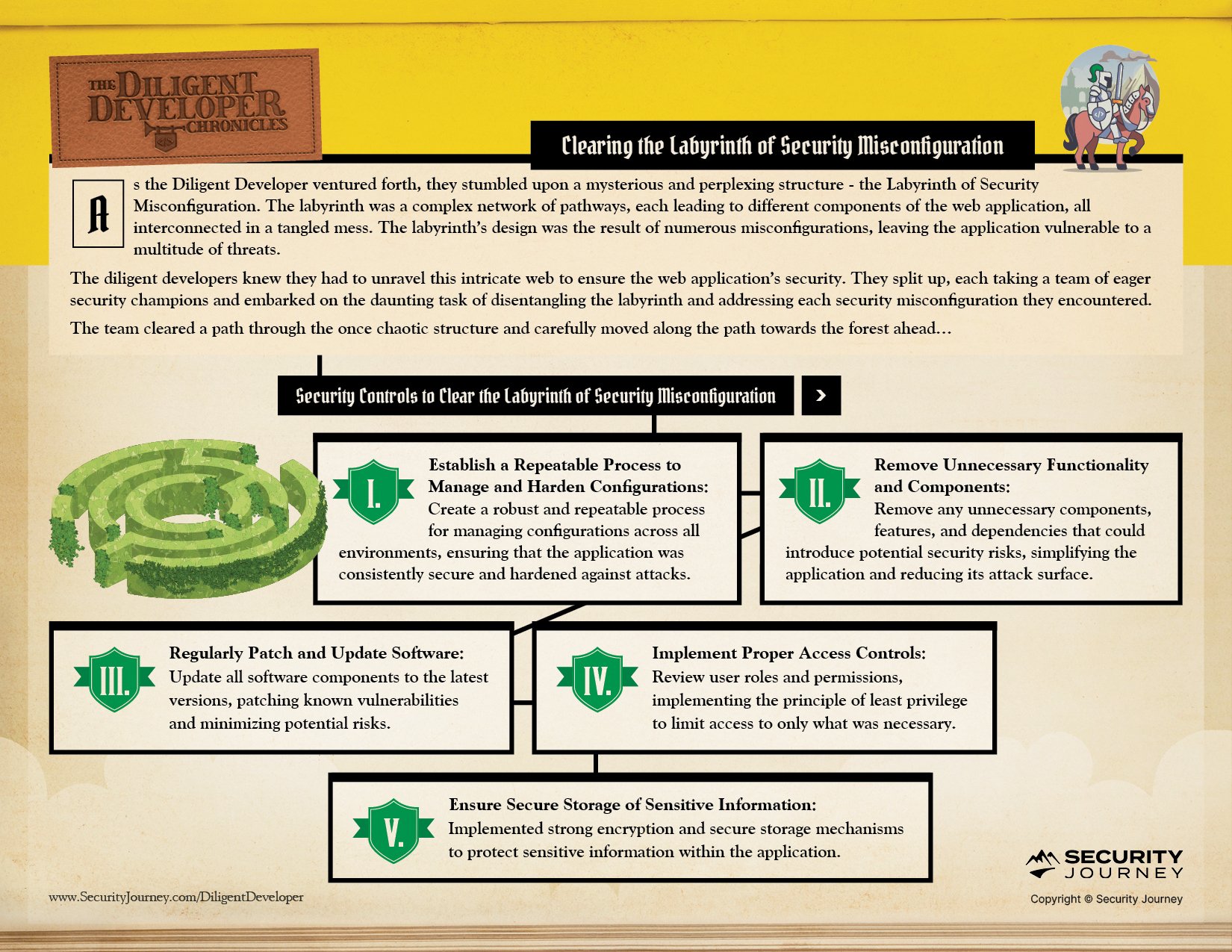
Implement a robust and repeatable process for managing configurations across all environments, ensuring the application is consistently secure and hardened against attacks.
Remove unnecessary components, features, and dependencies that could introduce potential security risks, simplifying the application and reducing its attack surface.
Update all software components to the latest versions, patching known vulnerabilities and minimizing potential risks.
They meticulously reviewed user roles and permissions, implementing the principle of least privilege to limit access to only what was necessary.
Implement strong encryption and secure storage mechanisms to protect sensitive information within the application.
Bring The Diligent Developers to Your Organization
Our AppSec experts at Security Journey recommend that developers don’t just take annual training on the most current OWASP Top 10 to be aware of prominent vulnerabilities and code risks but to have continuous training and conversations about code security in your organization.
But why not have fun in the process?
Security Journey developed The Diligent Developer Security Awareness & Education Program as a fun way to not only enhance security awareness, but to build skills across your development team to empower them to think securely. This could be added to National Cybersecurity Awareness month initiatives for the entire development team or be used to engage/grow a security champions program -- whatever works best for your organization.
In Chapter Five, The Diligent Developers take on The Labyrinth of Security Misconfiguration:
As The Diligent Developers continue on their journey, stay tuned to see what OWASP Top 10 Challenge they take on next.
Visit our webpage to learn more about accessing program materials and a program guide to train your organization on OWASP Top 10 vulnerabilities effectively.


