Published on
After you take the time to build your application, the last thing you want to see is someone come in and take it over, but SSRF attacks have happened to the most prominent names on the internet.
This article will review Server-Side Request Forgery, commonly known as SSRF, and how you can protect against SSRF attacks.
Read More About OWASP Top 10: OWASP Top 10 Software and Integrity Failures Explained
What is Server-Side Request Forgery?
Server-side request forgery (SSRF) is a web security vulnerability that allows an attacker to induce the server-side application to request an unintended location. This can be used to access sensitive data, execute arbitrary commands, or even take control of the server.
SSRF vulnerabilities can occur in various ways, but they typically involve the application being able to request arbitrary URLs. This can happen if the application:
- Takes user input and uses it to construct a URL
- Uses a hard-coded URL that is not properly sanitized
- Exposes an API that allows users to make requests to arbitrary URLs
Real-Life Example of Server-Side Request Forgery: Minecraft Server Attack
In 2018, an SSRF vulnerability was found in the Minecraft server software. The vulnerability allowed attackers to request the Minecraft server, which they used to execute arbitrary commands and take control of the server.
In some cases, the attackers used the compromised servers to launch denial-of-service attacks against other servers. In other cases, the attackers used the compromised servers to steal data from players.
The vulnerability was patched by Mojang, the developer of Minecraft, in October 2018. However, the vulnerability had been exploited for several months before being restored.
How Can You Protect Against Server-Side Request Forgery?
The key to protecting against SSRF attacks is to prevent the application from requesting unauthorized hosts. This can be done by:
Implement measures to limit outbound traffic from the application server to minimize the impact of potential SSRF attacks and reduce the risk of unauthorized access to internal systems.
Build out a strong allowlist of trusted domains and IP addresses, ensuring that the server only requests authorized and verified destinations.
Implement thorough security measures that involve sanitizing user input to prevent potential risks. Carefully validate and cleanse user-supplied data to ensure no unsafe or untrusted information could manipulate server requests.
Establish a system for monitoring and logging network activity to detect and respond to any suspicious or malicious activity that may indicate ongoing SSRF attacks or related threats.
Bring The Diligent Developers to Your Organization
Our AppSec experts at Security Journey recommend that developers don’t just take annual training on the most current OWASP Top 10 to be aware of prominent vulnerabilities and code risks but to have continuous training and conversations about code security in your organization.
But why not have fun in the process?
Security Journey developed The Diligent Developer Security Awareness & Education Program as a fun way to enhance security awareness and build skills across your development team to empower them to think securely. This could be added to National Cybersecurity Awareness Month initiatives for the entire development team or be used to engage/grow a security champions program -- whatever works best for your organization.
In Chapter Nine, The Diligent Developers are Building the Wall of Server-Side Request Forgery:
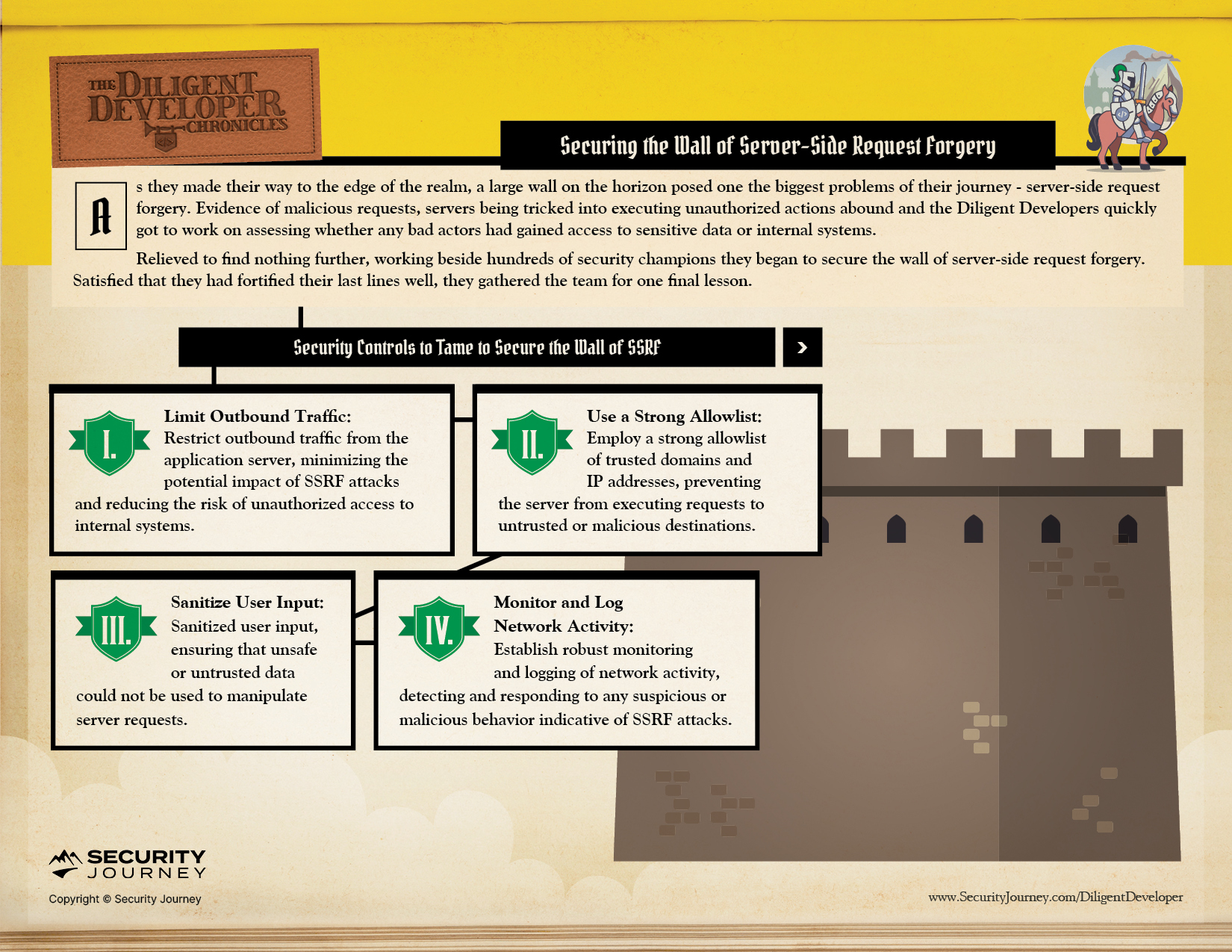
As The Diligent Developers continue their journey, stay tuned to see what OWASP Top 10 Challenge they take on next.
Visit our webpage to learn more about accessing program materials and a program guide to effectively train your organization on OWASP Top 10 vulnerabilities.


