Published on
Organizations that develop software know that application security is a top priority. Safeguarding customer data is critical.
There are many rules, regulations, and frameworks in place to protect sensitive data. You must understand and follow some or all, depending on the type of applications you develop and the industry you’re in.
AppSec compliance is a big topic, one far too large to cover in a single post. This guide helps you understand the most common application security compliance requirements for training developers.
Let’s start with the oldest and best-known data security obligation – PCI DSS.
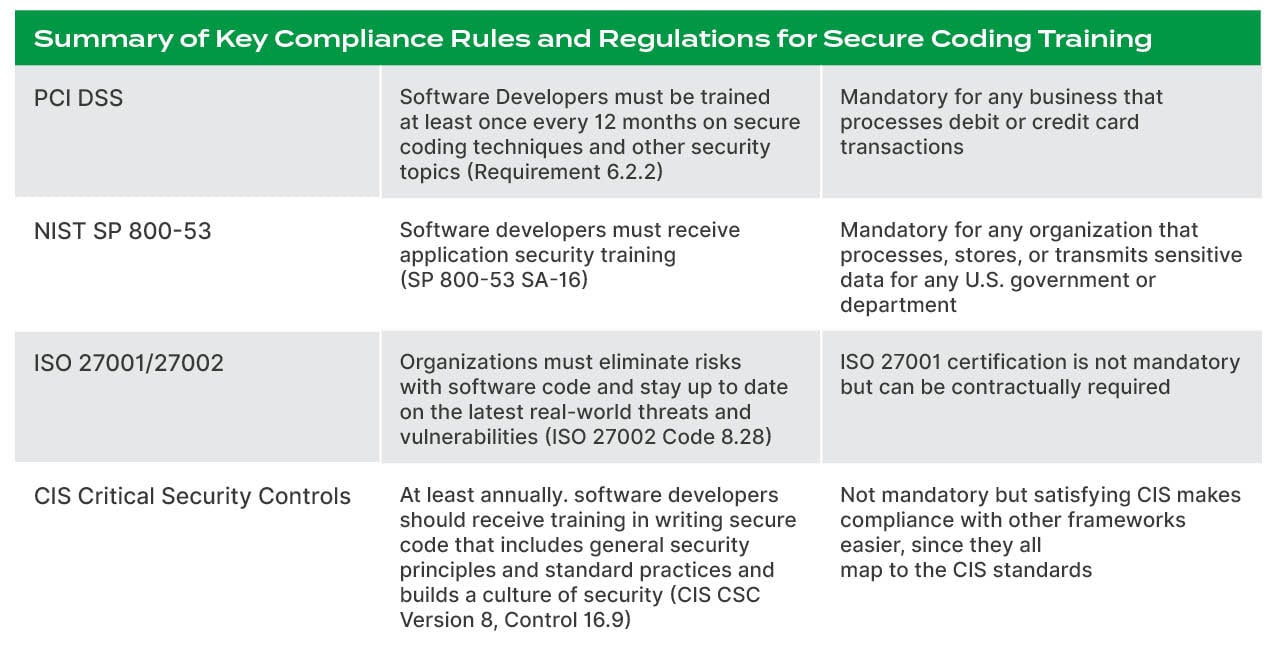
PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) is designed to safeguard credit and debit card transactions against fraud. This collection of requirements was created in 2004 by Visa, MasterCard, Discover, JCB International, and American Express.
Who should follow PCI DSS?
Compliance is mandatory for any business that processes credit or debit cards. If your application involves payments, PCI DSS has you in its compliance crosshairs.
What does PCI DSS say about developer training?
PCI DSS was recently updated, with Version 4 released in March 2022. With regards to developer training, PCI DSS v.4 Requirement 6.2.2 (a replacement to earlier PCI DSS Requirement 6.5) says:
“Software development personnel working on bespoke and custom software are trained at least once every 12 months as follows:
- On software security relevant to their job function and development languages.
- Including secure software design and secure coding techniques.
- Including, if security testing tools are used, how to use the tools for detecting vulnerabilities in software.”
PCI DSS is just the tip of the compliance iceberg. There are other obligations out there, too.
NIST
The National Institute of Standards and Technology (NIST) is part of the U.S. Department of Commerce and works with businesses and academia to strengthen economic security. NIST Special Publication 800-53 is part of their Risk Management Framework.
Who should follow NIST Special Publication 800-53?
If your organization is processing, storing, or transmitting sensitive data for the Department of Defense (DoD), NASA, the General Services Administration (GSA), or other government agencies, you must meet the requirements of the NIST Risk Management Framework. The framework has a multitude of subsections that offer instructions on how to follow it.
What does NIST Special Publication 800-53 say about developer training?
One of these subsections is NIST Special Publication 800-53, subsection SA-16. It requires “the developer of the system, system component, or system service to provide the following training on the correct use and operation of the implemented security and privacy functions, controls, and/or mechanisms.” Each organization defines what the “following training” will be.
In plain language, this means developers should get application security training. It gives the organization latitude in deciding the type of training to offer, including web-based, computer-based, classroom-style, and hands-on.
ISO 27001/27002
The International Organization for Standardization (ISO) created the ISO 27001 certification to identify organizations with Information Security Management Systems (ISMS) that meet global ISO standards. ISO 27002 is a subset of ISO 27001. It’s a collection of controls designed to provide guidance related to risk mitigation during the ISO 27001 certification process.
Who should follow ISO 27001/27002?
Obtaining ISO 27001 certification proves to your customers that information security is a priority for your organization. While it isn’t mandatory in the U.S. or most other countries, the certification can give you a competitive advantage in the marketplace. Some customers may include a clause requiring ISO 27001 certification in their contract with you.
What does ISO 27001/27002 say about developer training?
ISO 27002 Code 8.28 calls on organizations to eliminate risks associated with software code and stay up to date on the latest real-world vulnerabilities and threats. Providing secure coding training to developers is one strategy organizations can put in place to meet the intent of Code 8.28.
CIS
The Center for Internet Security (CIS) is a non-profit collective of global cybersecurity and IT experts from business, government, and academia. Together they develop standards and best practice guidance for cybersecurity. CIS manages the Critical Security Controls (formerly the SANS Top 20), which are incorporated into many legal, regulatory, and compliance frameworks.
Who should follow CIS Critical Security Controls?
The idea behind the creation of the CIS guidelines is to help organizations understand and achieve higher levels of cybersecurity. Since CIS guidelines are mapped to many other compliance frameworks, organizations can follow the CIS guidelines to help meet a variety of compliance obligations.
What does CIS CSC say about developer training?
CIS Critical Security Controls Version 8 was released in 2021. In it, the need for secure coding training for developers is specified. Control 16.9 states:
“Ensure that all software development personnel receive training in writing secure code for their specific development environment and responsibilities. Training can include general security principles and application security standard practices. Conduct training at least annually and design in a way to promote security within the development team and build a culture of security among the developers.”
Other Rules and Regulations to Know About
Beyond these specific compliance obligations that call out developer training, there are other rules and regulations to keep on your radar.
- Executive Order 14028 – Issued by President Biden on May 12, 2021, the order was designed to improve the nation’s cybersecurity. It requires government agencies to strengthen cybersecurity and the software supply chain. It requires secure software development environments and software bill of materials (SBOM), among other things.
- SOC2 – Service Organization Control 2 (SOC 2) is a framework that finds how well an organization meets five trust criteria related to data handling and storage – security, availability, processing integrity, confidentiality, and privacy. SOC2 Type 1 is a review of a company’s cybersecurity policies. SOC2 Type 2 is an audit of those policies and their effectiveness.
- FTC Safeguards Rule – The Federal Trade Commission’s effort to protect the private information of consumers. If your organization falls within the reach of this rule, it must “develop, implement, and maintain an information security program with administrative, technical, and physical safeguards designed to protect customer information.”
- HIPAA/HITRUST - The Health Insurance Portability and Accountability Act (HIPAA) protects the confidentiality of patient health information. One important part of HIPAA is the secure storage and transmission of patient data. HITRUST is the certification that proves an organization is HIPAA compliant.
Compliant vs. Secure
Being compliant is a necessary part of application development today. But compliance does not equal security.

Yes, you can tick the box to meet your compliance obligations and get a thumbs up from regulators. But true application security requires moving beyond this "bare minimum" mindset.
The best defense against cyber vulnerabilities and threats is to build a security culture across your entire organization. From the C-suite down, everyone must understand and embrace a security-first approach. And that begins with security training and education for developers and everyone involved with software development.


